# requirement: python2, git
$ apt update upgrade
$ apt install python2 git
$ git clone https://github.com/ciku370/hasher
$ cd hasher
$ python2 hash.py
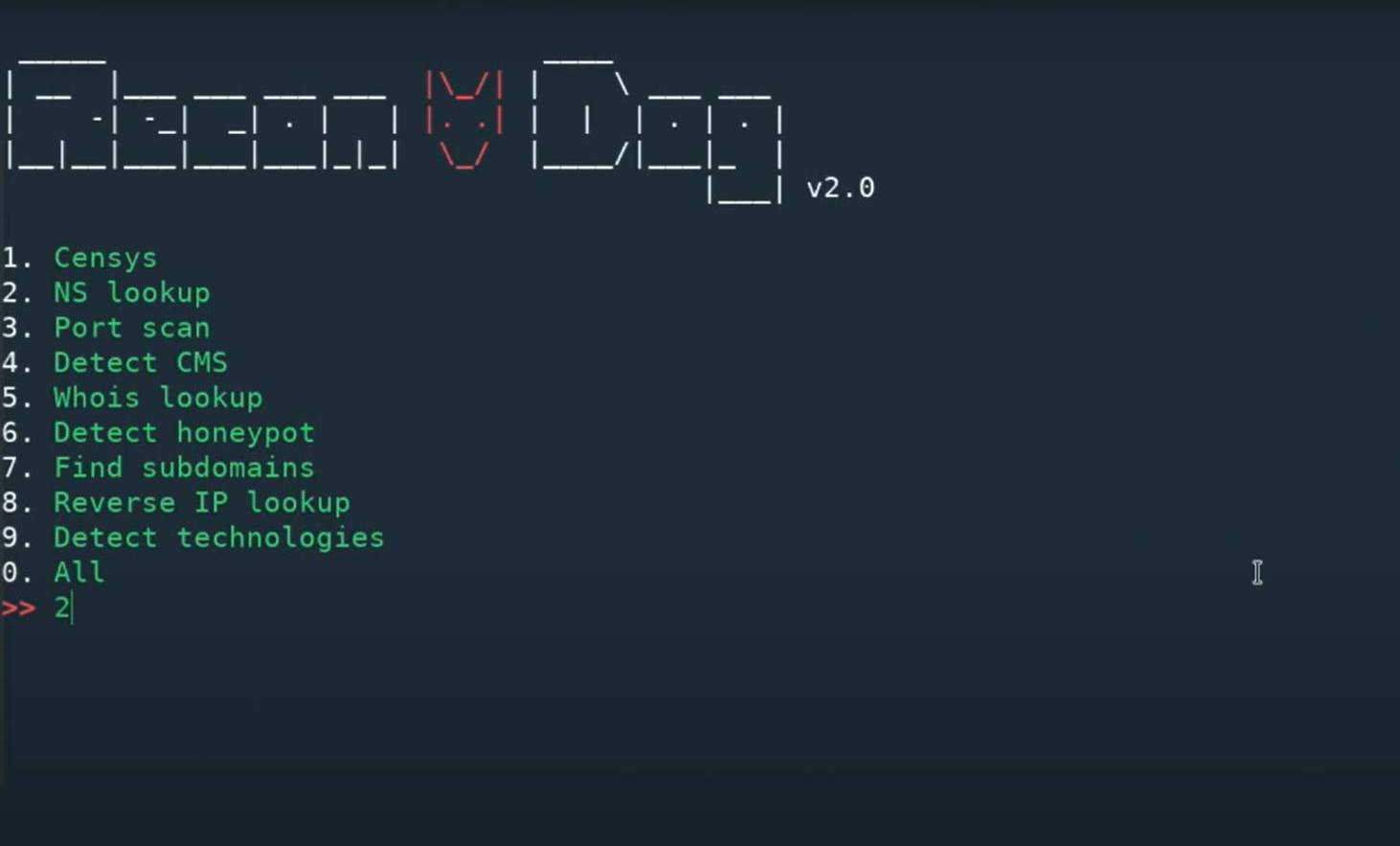
Recon Dog : Reconnaissance Swiss Army Knife
Main Features
Wizard + CLA interface
Can extracts targets from STDIN (piped input) and act upon them
All the information is extracted with APIs, no direct contact is made to the target
Utilities
Censys: Uses censys.io to gather massive amount of information about an IP address.
NS Lookup: Does name server lookup
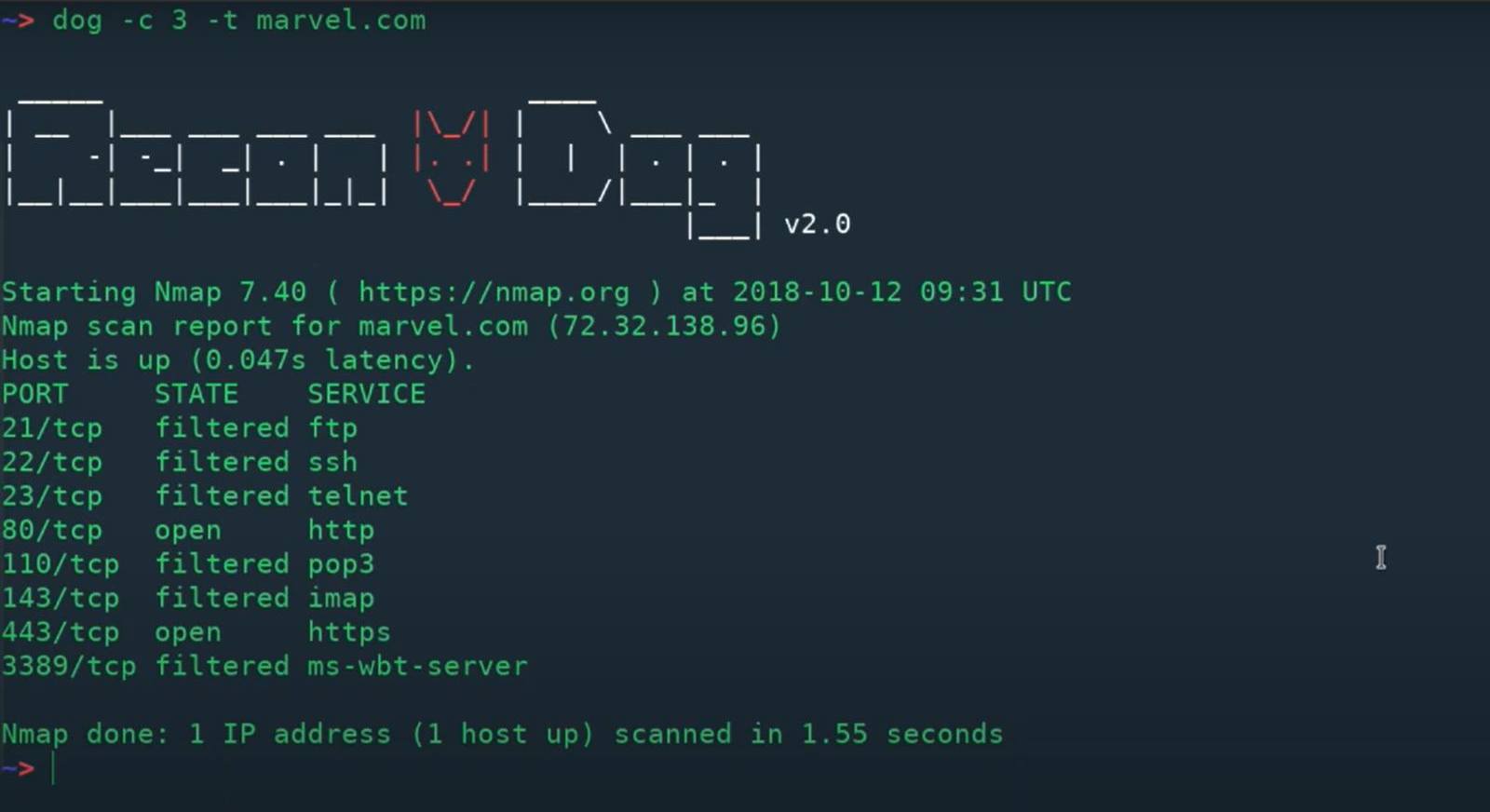
Port Scan: Scan most common TCP ports
Detect CMS: Can detect 400+ content management systems
Whois lookup: Performs a whois lookup
Detect honeypot: Uses shodan.io to check if target is a honeypot
Find subdomains: Uses findsubdomains.com to find subdomains
Reverse IP lookup: Does a reverse IP lookup to find domains associated with an IP address
Detect technologies: Uses wappalyzer.com to detect 1000+ technologies
All: Runs all utilities against the target
#Download Link
https://github.com/s0md3v/ReconDog
_,.-------.,_
,;~' '~;,
,; ;,
; ;
,' ',
,; ;,
; ; . . ; ;
| ; ______ ______ ; |
| `/~" ~" . "~ "~' |
| ~ ,-~~~^~, | ,~^~~~-, ~ |
| | ):( | |
| l / | \ ! |
.~ (__,.--" .^. "--.,__) ~.
| ---;' / | \ `;--- |
\__. \/^\/ .__/
V| \ / |V
| |T~\___!___!___/~T| |
| |`IIII_I_I_I_IIII'| |
| \,III I I I III,/ |
\ `~~~~~~~~~~' /
\ . . /
\. ^ ./
^~~~^~~~^
.Gt
j#W: ; GEEEEEEEL
;K#f .DL ,;;L#K;;.:KW, L
.G#D. f. :K#L LWL t#E ,#W: ,KG
j#K; EW: ;W##L .E#f t#E ;#W. jWi
,K#f ,GD; E#t t#KE#L ,W#; t#E i#KED.
j#Wi E#t E#t f#D.L#L t#K: t#E L#W.
.G#D: E#t E#jG#f L#LL#G t#E .GKj#K.
,K#fK#t E###; L###j t#E iWf i#K.
j###t E#K: L#W; t#E LK: t#E
.G#t EG LE. fE i tDj
;; ; ;@ :
*** Welcome to the GWTX console! Type 'help' for available commands ***
[ This tool is a custom console designed for exploiting targets ]
[ and performing various network-related tasks.It provides a command-line ]
[ interface for executing commands and managing options. ]
gwtx > set ip 157.122.154.154
[info] --> Set ip to 157.122.154.154
gwtx > set payload locate
[info] --> Set payload to locate
gwtx > exploit
[info] Starting Exploit On 157.122.154.154
[info] Running payload 'tools/locate.py' against target: 157.122.154.154
IP Location Information:
IP Address: 157.122.154.154
Country: China
City: Shenzhen
Zip Code:
Latitude: 22.5431
Longitude: 114.058
[complete] Scan Complete