[Feedback tracking] Fine-grained personal access tokens #36441
Replies: 213 comments 343 replies
-
|
I'm wondering, is there/will there be a way to create a fine-grained token for a repository one has collaborator permissions on? Such repositories don't seem to appear in the repository list, and no separate entries on the resource owners list are shown for such repositories. |
Beta Was this translation helpful? Give feedback.
-
|
Could this be extended to SSH keys as well? My work keys don't really need access to my personal repositories, and vice versa. I'd also like the ability to use GnuPG authentication subkeys for SSH without adding them separately, but that's another issue. Scoping them on a subkey-by-subkey basis would still be an improvement. |
Beta Was this translation helpful? Give feedback.
-
|
Will there be a way to create tokens that don't expire for CI? |
Beta Was this translation helpful? Give feedback.
-
|
Is there an API for creating these access tokens? Been playing with Hashicorp Vault and would love to use these tokens to build a Vault Secrets Engine plugin. |
Beta Was this translation helpful? Give feedback.
-
|
Expiry means I can't set it and forget it, and that's the entire point of granular access tokens - namely, the risk is zero because the permissions are tightly scoped. Forced expiry also means folks will just come up with trivial ways to reissue new ones, which will defeat the purpose anyways. It's like a forced password reuse policy - it seems like it helps security, but it actually harms it. I hope you'll reconsider forced expiry. |
Beta Was this translation helpful? Give feedback.
-
|
In order to facilitate transitioning between classic PATs and fine-grained, will it be possible to enable classic PAT functionality for specific users, but disable them for all others? It makes the transition a lot more manageable from a security perspective if organizations could disable classic PATs for standard users, but keep them enabled for users that have tokens created that are integrated into automated systems that will take time to migrate. |
Beta Was this translation helpful? Give feedback.
-
|
Loving the feature 🎉 Of the listed things on the roadmap, multi-org support and packages (GHCR) API would be very useful! Regarding the token expiry, is there some way to get notified ahead of time? |
Beta Was this translation helpful? Give feedback.
-
|
Ahhh I just spent half of my day trying to use a fine-grained token to download a private package; I overlooked the note with the list of unsupported API endpoints in this section of the documentation. I didn't figure it out until I saw the bullet points at the end of this thread! That was pretty clearly user error, but I'm posting this to see if this was a common mistake others encountered, in which case it could be useful for User Experience to take another look and see if this info could be made more prevalent. For example, maybe it could be presented outside of a box or in a red "warning" box. Or the bullet point could be less verbose (separate out the link to the supported endpoints); or the sub-list items could exclude the extra words "REST API to manage", making them easier to process. But I think my main source of confusion was that when I was reading too quickly and I saw "only work with personal access tokens (classic)", I thought it was going to be a list of things that only work with PATs. So it might be clearer to frame it instead as things that "are not supported for fine-grained personal access tokens". |
Beta Was this translation helpful? Give feedback.
-
Beta Was this translation helpful? Give feedback.
-
|
Will be nice to have source IP restriction on GH token similar to AWS IAM Roles (https://aws.amazon.com/premiumsupport/knowledge-center/iam-restrict-calls-ip-addresses/) |
Beta Was this translation helpful? Give feedback.
-
|
The mandatory expiration makes sense for human-oriented use cases - e.g. testing some scripts, locally running programs which interact with GitHub API etc. I have had a number of tokens I created in the past which I only discovered as still active some months or years later. However, for tokens which are used by machines - such as in a CI - the manual rotation seems like unnecessary overhead, as was already mentioned. Contrary to some suggestions made here though, I would say that instead of just allowing no expiry, it would make sense to somehow allow establishment of a trust relationship, such that GitHub backend does the token rotation and humans don't even need to ever see the token, let alone copy and paste it - hence further decreasing the chance of leaks. This would make sense IMO at least for the common case when the token is used within GitHub Actions. GitHub already essentially does that with the default I don't know what the best UX for cross-org and cross-repo tokens is, but perhaps there's some inspiration to take from impersonation mechanisms in GCP, AWS or HashiCorp Vault? Active trust relationships is probably something users would still need to be reminded of regularly, but at least it takes a lot of the overhead away and arguably makes it safer by not exposing the token to humans. |
Beta Was this translation helpful? Give feedback.
-
Beta Was this translation helpful? Give feedback.
-
|
Hello, PS Am I "blind" to find and it is in place? |
Beta Was this translation helpful? Give feedback.
-
|
Seems like a great feature! However, I can't seem to generate a token which accesses specific repositories? Not sure if I'm totally missing something here. |
Beta Was this translation helpful? Give feedback.
-
|
Will there be a way to associate fine-grained token with team? For example, I am a member of some teams named |
Beta Was this translation helpful? Give feedback.
-
|
I would really like to see respect for the Notifications / Custom Routing options for email that I have set in my account depending on the Organization for which the PAT is granted permissions. This should be easily determined based on the Resource Owner choice we make when creating the token. Right now all my email addresses are blasted when I have an expiring token even when only one of those email addresses is relevant to the token in question. Without thinking too carefully about it, I could imagine security implications if there is a malicious administrator with access to one of my email boxes being alerted to the existence of irrelevant tokens. |
Beta Was this translation helpful? Give feedback.
-
|
After experimenting with the REST API, it seems like there is mismatch between the ID of a fine grained PAT through the |
Beta Was this translation helpful? Give feedback.
-
|
How would I revoke a token that I find somewhere? Say, I don't have access to the account that made it (or even dont have a github account at all), but want to revoke a token that I found leaked that the secret scanning didn't find. As far as I can see, the only way to revoke a token without access to the account would be to publish it in a public gist, which seems a bit silly. I feel there should be a UI somewhere that you can paste token(s) into to revoke them. |
Beta Was this translation helpful? Give feedback.
This comment was marked as off-topic.
This comment was marked as off-topic.
-
|
Hey, the most important feature with fine-grained PATs that is currently stopping us from migrating 100% from classic tokens is the ability to use these tokens to be able to add GitHub Apps to Repositories. From what we can see here, fine-grained tokens support only limited Apps endpoints. Is there any time-line for fine-grained PATs to support adding GitHub Apps to repositories? Thanks in advance! |
Beta Was this translation helpful? Give feedback.
This comment was marked as off-topic.
This comment was marked as off-topic.
This comment was marked as off-topic.
This comment was marked as off-topic.
-
|
Mark as answered 🙏🏾 |
Beta Was this translation helpful? Give feedback.
-
|
I contacted support earlier this year about the "Checks" repository permissions not being available for fine-grained personal access tokens yet, and they confirmed it was not available despite documentation indicating otherwise: https://docs.github.com/en/rest/checks/runs?apiVersion=2022-11-28#list-check-run-annotations--fine-grained-access-tokens |
Beta Was this translation helpful? Give feedback.
This comment was marked as off-topic.
This comment was marked as off-topic.
-
|
Do I see it correctly that as of today, the projects permission can only be selected for resources owned by an organization, but not a personal account, is that right? So for a personal account, you still need a classic PAT to interact with projects? |
Beta Was this translation helpful? Give feedback.
-
|
It's not clear what permissions are required for GraphQL queries because all of the fine-grained PAT documentation points to REST endpoints. I’ve got a GraphQL query (using
The PAT is scoped to a specific repository ( The queryquery GetViewerStargazers($cursor: String) {
viewer {
login
starredRepositories(first: 100, after: $cursor) {
isOverLimit
totalCount
pageInfo { endCursor hasNextPage }
edges {
node {
archivedAt
description
forkCount
homepageUrl
url
isFork
isPrivate
isTemplate
languages(first: 5, orderBy: { direction: DESC, field: SIZE }) {
edges {
node {
name
}
size
}
totalCount
totalSize
}
latestRelease { name publishedAt }
licenseInfo { nickname spdxId }
nameWithOwner
parent { nameWithOwner }
pushedAt
repositoryTopics(first: 20) {
totalCount
nodes {
topic { name }
url
}
}
stargazerCount
}
starredAt
}
}
}
}The response: {
response: {
url: 'https://api.github.com/graphql',
status: 502,
headers: {
'access-control-allow-origin': '*',
'access-control-expose-headers': 'ETag, Link, Location, Retry-After, X-GitHub-OTP, X-RateLimit-Limit, X-RateLimit-Remaining, X-RateLimit-Reset, X-OAuth-Scopes, X-Accepted-OAuth-Scopes, X-Poll-Interval, X-GitHub-Media-Type, Deprecation, Sunset',
'content-type': 'application/json',
date: 'Mon, 21 Oct 2024 17:04:24 GMT',
server: 'github.com',
'transfer-encoding': 'chunked',
vary: 'Accept-Encoding, Accept, X-Requested-With',
'x-github-request-id': 'E238:17113B:3A205E:6F5559:6716898E'
},
data: { data: null, errors: [Array] }
}If this is a permissions error, it could be a lot clearer. (It's also not clear to me where this error should be reported.) |
Beta Was this translation helpful? Give feedback.
-
|
Any chance we can have fine-grained tokens for only selected gists? |
Beta Was this translation helpful? Give feedback.
-
|
Every time I need to dig up my projects I struggle with tokens. There is a too long list of irrelevant features, but no feature just to fetch and push new changes. Can you make a simple button or a guide for minimal list of requirements for token to be able to clone a project and push some changes to it for dummies like me? |
Beta Was this translation helpful? Give feedback.
-
|
Re 
That doesn't look promising. I was just looking into this yesterday as I wanted to access a package in my personal account but don't want to create a token that has access to other organizations that I'm a member of (like e.g. my employer). Not being able to create even an organization-scoped token to access packages makes packages/ghcr.io unusable if you use organizations and care about security. @ankneis do we have any hope of a solution to this, given the seeming de-prioritization? |
Beta Was this translation helpful? Give feedback.
-
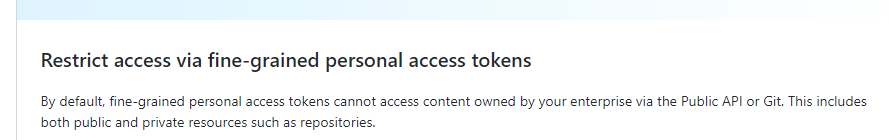
This topic serves as an area for feedback and discussion on the new fine-grained personal access tokens format, launched on October 18th. It includes more permissions, mandatory expirations, and organization + repository scoping. You can find more details in the blog post and the documentation.
There are some limits to fine-grained PATs that we'll be addressing in the coming months:
Recently, we've added:
There are also some APIs that do not yet support the fine-grained permission model, that we'll be adding support for in time:
Please let us know what you'd love to see in this new token type, what worked for you, and what didn't. Thank you!
Beta Was this translation helpful? Give feedback.
All reactions