A simple script to patch smali file to include a Fake Security Provider at 1. This provider is created by patching the SpongyCastle library to print the key, key size, algorithm parameters, keystore password in logcat. With this you can retrieve application cryptographic assets provided applications depend on the default security provider.
If applications just rely on default Security Provider like this
Cipher.getInstance("AES");
KeyStore.getInstance("BKS");then inserting a security provider
Security.insertProviderAt(new BouncyCastleProvider(), 1);can divert all the cryptographic operations to be performed through the inserted security provider.
sh patchcryptoprovider.sh <xyz.apk> <class file to include the security provider>Ex: sh patchcryptoprovider.sh 123.apk MainActivity
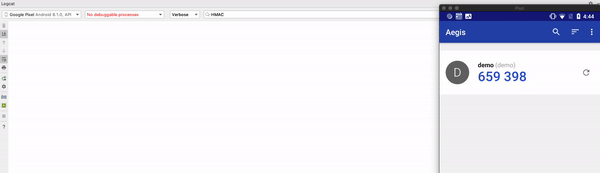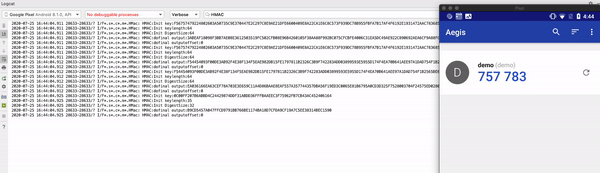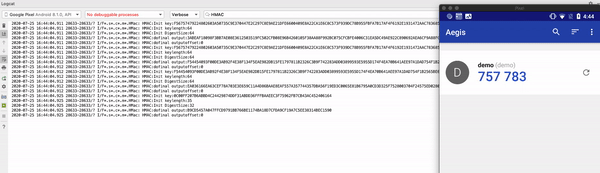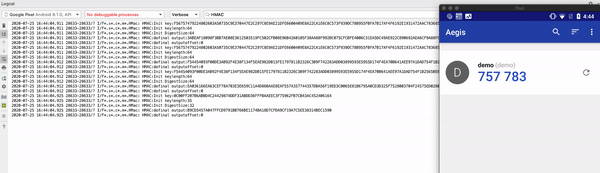
Aegis OTP authenticator depends on the default Security Provider. By executing this script, this app is tampered with a fake security provider and hence OTP seed used in HMAC operation can be seen easily in the logcat