A simple drop-in HTTP proxy for transparent LDAP authorization which is also a HTTP auth backend.
You can use pinepain/ldap-auth-proxy docker image (see available tags here)
or build binary by yourself, Dockerfile and .travis.yml list all necessary steps to build it.
Usage examples could be found in examples folder.
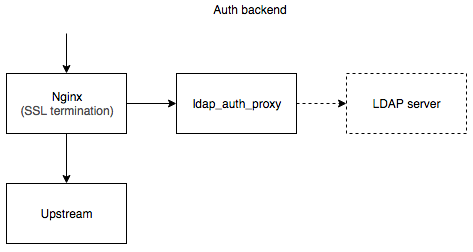
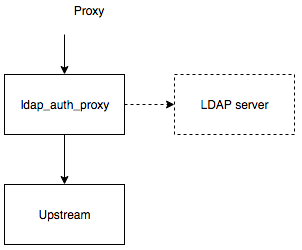
LDAP auth proxy could be used in two modes: as an auth backend and as a proxy:
Examples:
- Kubernetes
ingress-nginxsetup could be found in examples/k8s-ingress-nginx. docker-composesetup could be found in examples/auth_backend.
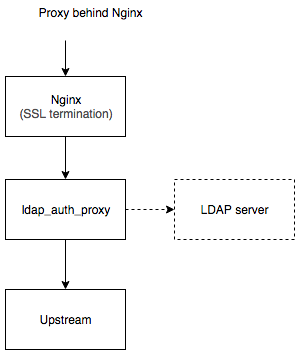
and it's variation, proxy behind nginx:
Example docker-compose setup could be found in examples/proxy
export LDAP_SERVER='ldaps://ldap.jumpcloud.com'
export LDAP_BASE='o=<oid>,dc=jumpcloud,dc=com'
export LDAP_BIND_DN='uid=<bind user name>,ou=Users,o=<oid>,dc=jumpcloud,dc=com'
export LDAP_BIND_PASSWORD='<bind user password>'
export LDAP_USER_FILTER='(uid=%s)'
export LDAP_GROUP_FILTER='(&(objectClass=groupOfNames)(member=uid=%s,ou=Users,o=<oid>,dc=jumpcloud,dc=com))'
export GROUP_HEADER='X-Ldap-Group'
export HEADERS_MAP='X-LDAP-Mail:mail,X-LDAP-UID:uid,X-LDAP-CN:cn,X-LDAP-DN:dn'
where <oid> is your organisation id.
A zero length password is always considered invalid since it is, according to the LDAP spec, a request for
"unauthenticated authentication." Unauthenticated authentication should not be used for LDAP based authentication.
See section 5.1.2 of RFC-4513 <http://tools.ietf.org/html/rfc4513#section-5.1.2>_ for a description of this behavior.
Neither zero length username supported. Anonymous authentication should also not be used for LDAP based authentication.
See section 5.1.1 of RFC-4513 <http://tools.ietf.org/html/rfc4513#section-5.1.1>_ for a description of that behavior.
ldap-auth-proxy is licensed under the MIT license.